At CloudZen, our team consistently aligns with the AWS Shared Responsibility Model when working on customer projects. In this model, AWS secures the underlying cloud infrastructure, while customers are responsible for safeguarding their data, applications, and configurations. By adhering to these clear security boundaries, we help minimize risks, enhance compliance, and ensure a robust security posture for our clients.
AWS Responsibilities: Security "of" the Cloud
AWS is responsible for the security of the overall cloud environment. This includes:
- Physical Security – AWS secures data centers with multi-layered security, including surveillance, access controls, and environmental protections.
- Network & Infrastructure Security – AWS maintains and protects the global infrastructure, including compute, storage, networking, and database services.
- Hardware & Software Maintenance – AWS regularly patches and updates its infrastructure to address vulnerabilities and enhance security.
- Compliance & Certifications – AWS undergoes compliance audits for standards like ISO 27001, SOC 2, PCI DSS, HIPAA, ensuring its cloud platform meets industry security requirements.
CloudZen Innovations Customer Case study
CloudZen Innovations’ customer, a leading enterprise financial institution, leverages Amazon S3 for storing sensitive customer data. They rely on AWS to handle data durability, infrastructure security, and physical data center protection, eliminating concerns about server patching or physical security risks. This allows them to focus on data governance, compliance, and access control while benefiting from AWS’s robust security framework.
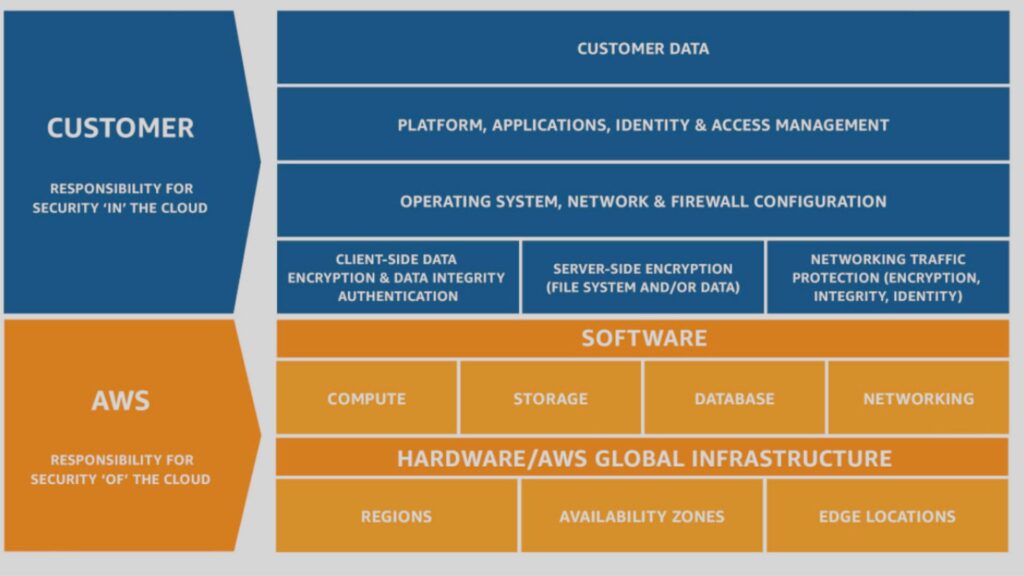
CloudZen Responsibilities: Security "in" the Cloud
CloudZen team helped customers to secure their applications, data, and access controls. Our key responsibilities include:
- Data Protection – Users must encrypt sensitive data using AWS services like AWS KMS (Key Management Service) and ensure backup policies.
- Identity & Access Management (IAM) – Properly configuring IAM roles and policies to enforce the principle of least privilege.
- Application Security – Securing workloads using AWS WAF, Shield, and Security Groups to prevent unauthorized access.
- Network Security – Configuring VPC security groups, Network ACLs, and enabling AWS GuardDuty to monitor threats.
- Compliance & Governance – Ensuring compliance with industry-specific regulations by configuring AWS services appropriately.
CloudZen Innovations SaaS customer case study:
CloudZen Innovations’ customer, a leading SaaS company deploying its application on Amazon EC2, is responsible for:
- Keeping the OS and application updated.
- Managing access using IAM and Multi-Factor Authentication (MFA).
- Encrypting customer data stored in RDS or S3.
AWS provides the infrastructure, but failure to secure the instance (e.g., using weak credentials or misconfigured security groups) could lead to data breaches.
The Importance of Understanding Shared Responsibility
Misconceptions about cloud security often led to breaches. Many assume AWS handles everything, but misconfigurations (e.g., public S3 buckets, weak IAM policies) are user mistakes, not AWS failures.
CloudZen’s Best Practices for Customer’s AWS environment:
- Use AWS Security Tools: Enable AWS Security Hub, AWS Config, and GuardDuty for continuous monitoring.
- Apply the Principle of Least Privilege: Restrict IAM permissions to only what’s necessary.
- Enable Logging & Auditing: Use AWS CloudTrail and AWS CloudWatch for visibility into user actions.
- Automate Security: Implement AWS Lambda functions for security automation and compliance enforcement.
Additional Technical Considerations for Security in the Cloud
Beyond the core responsibilities, CloudZen team also recommends considering advanced security measures:
- Incident Response & Recovery – Develop a well-documented incident response plan using AWS tools like AWS Security Hub and Amazon Detective.
- Data Lifecycle Management – Implement data retention policies using Amazon S3 Lifecycle Policies and AWS Backup.
- Continuous Compliance Monitoring – Use AWS Config to track resource configurations and enforce compliance with security policies.
- Zero Trust Architecture – Adopt a security model that requires continuous verification of users, devices, and applications before granting access.
- Container Security – If using AWS container services (EKS, ECS, or Fargate), ensure that IAM roles for tasks, image scanning, and network policies are well-configured.
- Multi-Account Security Strategy – Implement AWS Organizations and AWS Control Tower to enforce security policies across multiple AWS accounts.
- Encryption & Key Management – Use AWS Key Management Service (KMS) for centralized encryption key management.
- Threat Detection & Response – Leverage Amazon GuardDuty and AWS Security Hub to detect and mitigate threats in real time.
Conclusion
Understanding the AWS Shared Responsibility Model is critical for securing cloud workloads. While AWS ensures the infrastructure is secure, customers must proactively safeguard their data, applications, and configurations. CloudZen team always follows recommended best practices and leverages AWS security tools, organizations can strengthen customer’s cloud security posture and mitigate risks effectively.
Adopting a security-first mindset and continuously updating security strategies will help organizations stay ahead of evolving threats in the cloud landscape. Always keep learning, monitoring, and improving your cloud security approach for a resilient and compliant cloud environment.


